
News Archive
| Search |
Public Sources
All my github repos
Git repositories
logproc
ausadmin-web
get-cert
fat-set-uuid
djbdns
LS30
TRS-80
xbee-controller
alpine-mojo-base
docker-eagle
zmac
smallc
dc20
perl-sql-tools
avr-onewire
avr-fd-serial
get-cert
Electronics
Arduino RFID Door Lock
XBee network controller
Hardware
LS30 Burglar Alarm
Online store
Software
logrun
math-trainer
mp3cd-tools
fakepop
aunic-modify
ausadmin
sms-notify
apt-cacher
video-capture
wav-fixer
misc
TRS-80 software I wrote
System-80 Gallery
Zeta BBS
Utilities
Printer Utils
Patches
Operating Systems
Library of C
Languages
Include files
Hardware
Games
FORTRAN Programs
File Utils
Disk Utils
Comms Programs
CMD File Utils
BASIC Programs
Uni Assignments
Hats I wear
aus.* newsgroups
www.news-admin.org
Philosophy
New Technology
Ethical Internet Advertising
Digital Freedom
Anti-spam
Age of plenty
Ditch Windows
Technical
Big Server
Spam
Unclassified
Zeta Internet
Links
Your donation gives me time
to develop more cool free stuff
First exhibit in our little gallery
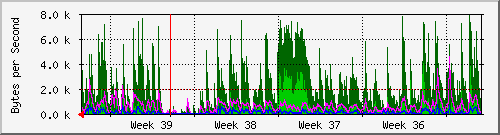
The green is the inbound traffic on my ADSL interface. The big chunky area in the middle is a sudden increase in spam received, mostly the Swen virus, being sent to multiple addresses I have used to post to USENET recently:
- nick-200307@nick-andrew.net
- nick-200308@nick-andrew.net
- nick-200309@nick-andrew.net
The intent of using multiple emails in my From headers was to time-limit the validity of an address, so I could receive emailed replies to postings for a while (my thought was 1 or 2 years) and after that time mail to the address would bounce. I had to rethink that strategy. It is clear that using multiple sender addresses just causes me to get multiples of the spam. Better to use an obscured address now I think.

This is the graph which alerted me to the problem. The sharp rise at the end of week 37 is the same as the hump in the previous graph. I noticed it at the end of week 37. Spam had used 25% of my T$ ADSL 3 gig quota in only 48 hours; I reacted immediately by moving my domain MX records to my colo server and installing qpsmtpd on it.
Qpsmtpd is an SMTP server which interfaces with qmail. It can reject SMTP traffic at any point in the SMTP transaction, before or after the message body. It has support for DNSRBL and greylisting, which uses SMTP temporary failure codes to force a sender to retry a message later. The theory with greylisting is that spammers do not code their MTAs to retry failed message attempts.
I configured qpsmtpd to reject all email to the three USENET addresses shown above as well as other addresses which have plagued me with spam such as ian@tull.net and jethro@tull.net or the puzzling crespou34@tull.net.
My domains have been used to forge spam sender addresses for several months now. Back in 1997 when this was done to zeta.org.au it was a real nuisance for me and the Zeta members, but nowadays nobody seems to care. It's happened to tull.net, nick-andrew.net and news-admin.org and it is a nuisance mostly for the double bounces - qmail would accept bounce messages addressed to nonexistent random users at those domains, then send a double bounce to me or to a nonexistent victim address. So I configured qpsmtpd to accept mail to certain known addresses at my domains and reject all mail to any other address. This is before the mail body is received of course.
I also added a text filter to qpsmtpd to detect the Swen virus. It works really well but unfortunately the design of qpsmtpd requires the message body to be received in full before the text filter can be run. That means that slim has received a bunch of these messages and deleted them. The additional inbound traffic caused slim to go well over its colo quota for the month and I received a bill for an additional $223.68.
I have now switched from T$ ADSL (3 gig quota) to iiNet, which is fixed price and provides 10 gigs peak, 6 gigs offpeak and shapes the connection if quota is exceeded. So I will now move my MX records back to my ADSL connection and implement the same kind of filtering at home.
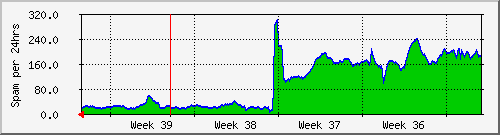
This graph shows the result of filtering the spam using qpsmtpd. It shows the number of spams caught per day by my spamassassin and blacklist filters. After qpsmtpd filtering was installed the spam level dropped dramatically from 200+ spams per day down to 20-24.
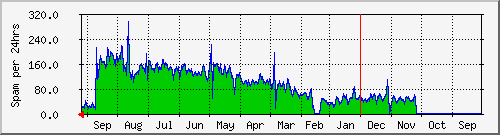
And I'll leave you with a worrisome picture. The spam situation is getting worse quite rapidly. This is the yearly graph which shows that the number of spams hitting my mail server has increased from around 60/day to 200/day in less than a year. No doubt a lot of this is because I have been active on USENET for a very long time. It seems old addresses are never forgotten and there are always more spammers. As a consequence I need industrial quality spam filtering. Thanks assholes.
