Due to the recently exposed ssh key generation vulnerability, many ssh keys may need to be deleted and recreated. This tool may help with that.
What it does is find all the ssh keys existing on several hosts and where those keys appear in .ssh/authorized_keys files. It collates the results from all hosts and writes a directed graph for the 'graphviz' tool, which helps to visualise which keys are providing access to which users.
The scan tool works by connecting to each specified host using ssh and executing a host script. The host script examines the user's .ssh directory and sends a report to STDOUT, which is received by the scan tool. The host script can also iterate through /etc/passwd and examine every user's .ssh directory.
Use graphviz to visualise the graph. How to use: firstly make a file 'host-list' of all hosts you have access to, one line per hostname. Include any hosts you have root access to just as the hostname, and if you have only user access, use "user@hostname". You need to run the scan tool from a place which can ssh to all these hosts -- as root for all hostnames listed in your 'host-list' file which are not qualified with a username.
scan-ssh-keys.pl $(cat host-list) > output.dot dot -Txlib output.dot
Use the mouse wheel to zoom in/out of the graph image. Use the mouse middle button to pan the image. You can also use 'dot' to write various output files such as JPEG or SVG.
Here is a sample graph produced by the scan tool. The graph resolution is deliberately reduced (to make the node labels unreadable) for security reasons. Also my full ssh key graph is somewhat larger than this :-)
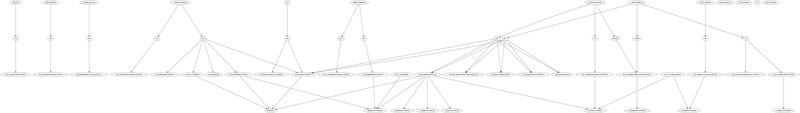
Later on I expect to enhance the scan tool to assist with adding and deleting ssh keys.
To download from my Mercurial repository, see: nick-src-regen-ssh-keys.